Hardware Wallets, Airgap Wallets, and Interstellar: A Comparison
Introduction
Hardware wallets like Ledger and airgap wallets like Polkadot Vault have brought essential improvements to the security of digital assets. They protect private keys from compromise through physical isolation or secure chip execution.
However, the evolution of threat models — particularly those involving AI-generated deception, UI spoofing, and supply chain vulnerabilities — has exposed the limitations of key-centric security models.
Interstellar is not just an addition to the security stack — it represents a new category of protection. While we acknowledge the legacy and utility of HWWs and airgap wallets, our aim is to offer a future-proof alternative that can ultimately replace these tools where appropriate — by securing the human layer, not just the cryptographic key.
This document compares Interstellar’s Intent Layer architecture to these traditional models, including critical aspects like approval clarity, supply chain risk, UX fidelity, recovery, and cost-to-security efficiency.
Comparative Overview
| Feature / Risk Vector | Ledger (HWW) | Polkadot Vault (Airgap) | Interstellar |
|---|---|---|---|
| Supply Chain Risk | Requires trusted shipping + firmware integrity | Requires secure offline setup | Uses existing mobile; avoids external hardware; TEE + SE integrity |
| UI/UX Clarity | Tiny screen, limited messages; easy to mislead | QR shows raw data; moderately clear | Full-screen visual cryptographic display; cognitive validation |
| Approval Attack Resistance | Susceptible to spoofed UI or dApp manipulation | Less exposed but requires user vigilance | Validates visual intent cryptographically; protected from spoofing |
| Recovery Model | Seed phrase (phishable, misstored) | Manual recovery with airgapped QR flow | No exported secret; deterministic recovery from secure file backup and NFC items |
| Device Cost & Distribution | $80–$300 per unit + logistics | Requires 2 secure smartphones | Zero hardware cost; mobile-native SDK |
| Security Cost Efficiency | High per-user hardware cost | High cost to ensure device integrity | Scales via existing hardware + secure software stack |
| Transaction Validation UX | Confusing for complex multisigs | Clearer but still manual | Transaction message rendered per-session via garbled circuits |
| Multisig UX Consistency | Each signer sees reduced info; no shared rendering | Separate device views; no enforced consistency | All signers see the same message rendered via device-specific garbled circuits — ensuring shared, validated intent |
| Legacy Device Integration | Native signer only | Native signer only | Compatible as signer via mobile-mediated interface (e.g. Ledger/Vault via Interstellar UX layer) |
| Multisig Compatibility | Used in Ledger + Safe stacks | Used in Substrate multisig | Flexible signer model: e.g., 2 Interstellar + 1 NFC tag + 1 SE card + 1 Vault |
| Attack Vectors Covered | Private key extraction, MITM | Remote signing compromise, app spoofing | Adds defense against perception fraud, UI spoofing, adversarial AI |
Real-World Example: Bybit + Safe + Ledger Exploit (Feb 2025)
In Feb 2025, a high-profile exploit targeted users of Gnosis Safe multisigs and Ledger hardware wallets within the Bybit ecosystem. Despite leveraging secure hardware and multisig design, attackers were able to:
- Manipulate dApp frontend logic to misrepresent transaction intent
- Exploit poor UX visibility on Ledger's limited display
- Trigger approvals that appeared legitimate but were in fact malicious
Reference: The attack has been analyzed in depth by multiple technical researchers including BlockSec and SlowMist. We recommend reviewing credible write-ups such as the SlowMist Labs Bybits Exploit Report.
Key lesson: Even with trusted hardware, the weakest link remains the perception and approval interface — not the cryptographic key.
Interstellar’s Advantage:
- Sensitive actions are rendered in full via cryptographic visual encoding (garbled circuits)
- Attackers cannot hijack the interface — only the real user sees and approves the intended action
- The system validates the intent, not just the cryptographic validity of the transaction
Multisig Integration: From Legacy Devices to Intent layer Nodes
Interstellar is designed to support multi-party approval flows that include both advanced mobile-native validation and legacy signer compatibility.
In an Interstellar-based multisig flow, all participants receive the same transaction message, but each message is rendered via a distinct garbled circuit bound to their device. This ensures a consistent, human-verifiable intent is shared across signers — while preserving cryptographic isolation and preventing spoofing.
This design addresses a critical weakness in traditional multisig setups, where signers often operate in isolation, with inconsistent or ambiguous transaction displays (e.g., as exploited in the Bybit + Safe + Ledger attack).
Interstellar could potentially also allows legacy signers such as Ledger or Polkadot Vault to be used via the mobile interface, benefiting from the visual cryptographic approval layer — even if the signing is completed externally.
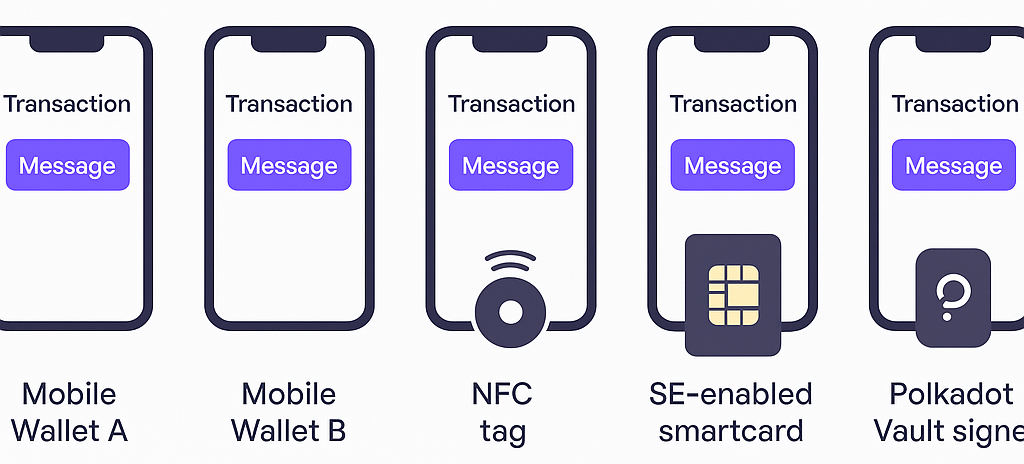
📦 Example Multisig Configuration (5 Signers)
All participants receive the same transaction message rendered via device-specific garbled circuits, ensuring consistent perception and validated intent.
- Mobile Wallet A — Interstellar mobile-only (no additional hardware)
- Mobile Wallet B — Interstellar mobile-only (no additional hardware)
- Mobile Wallet C — Bound to NFC tag for physical-local validation
- Mobile Wallet D — Bound to SE-enabled smartcard (Interstellar-trusted)
- Mobile Wallet E — Bound to Polkadot Vault signer (via Interstellar-trusted interface)
This hybrid approach balances ecosystem compatibility with user-centric security, ensuring that both the cryptographic layer and the human perception layer are secured by design.
The Hidden Cost of Airgap Integrity
While airgap wallets seem cost-effective, ensuring the actual integrity of an old smartphone is often prohibitively expensive:
- Requires full reset and de-Googleing
- Must disable baseband radios (airplane mode is not foolproof)
- Needs validated ROM or open-source firmware (e.g. GrapheneOS)
- No guarantee the supply chain of the second-hand device was uncompromised
By contrast, Interstellar:
- Uses the primary mobile device with embedded Secure Element
- Leverages TEE attestation and cryptographic proof of execution
- Avoids “DIY security theater” by integrating verifiable cryptographic isolation
A Note on Firmware Chain Integrity
We recognize that today’s hardware wallets (e.g. Ledger, Trezor, Keystone) benefit from highly secure and mature firmware integrity chains — including secure boot, anti-rollback protections, and verified firmware signing procedures. This makes them particularly strong in preventing unauthorized firmware updates and preserving device state trust.
However, in practice, this advantage has limited impact in preventing supply chain attacks, which often target:
- Physical device compromise before delivery (e.g., repackaged or cloned HWWs)
- Companion app hijacking or UI manipulation, where malicious intent is introduced long before firmware is even involved
Moreover, as mobile SEs (e.g., Titan M2, Apple SE) evolve, and platforms adopt verifiable execution environments such as TEE + visual cryptography, this firmware chain gap is expected to diminish and eventually disappear — particularly with the arrival of post-quantum SEs and nil-message compute paradigms.
In that context, Interstellar offers a more flexible and future-resilient architecture — one that trades hardware rigidity for real-time verifiability of user intent.
Conclusion
While hardware and airgap wallets have served the crypto community well, they do not address the growing problem of perceptual manipulation, cognitive spoofing, and UI-based deception.
Interstellar introduces a new trust model — one built around:
- Human cognition as a security anchor
- Visual and behavioral cryptographic validation
- Zero-export recovery without fragile phrases or additional devices
As attacks shift from stealing keys to stealing intent, Interstellar offers the layer that today’s wallets lack — and that tomorrow’s wallets will require.
Ready to see Interstellar in action? Jump to the Shortcut Path for Reviewers to evaluate Milestone 1 directly — no need to read the full documentation upfront.